)
In a case study, we found access to over 1,200 accounts associated with glucose monitors for sale on underground markets in the last year
Digitized medical information and records enable patients and medical professionals to access critical information instantly. However, this convenience comes at a cost; the Health Insurance Portability and Accountability Act (HIPAA) and its associated rules and regulations mandate that healthcare providers and data processors must ensure that protected health information (PHI) is properly secured.
Healthcare providers invest considerable resources in security, such as data encryption and hardening applications. However, the weak point might be the patients themselves. That is, if an attacker gains access to a patient’s account, they can also gain access to the PHI that it contains, posing regulatory concerns.
On the deep and dark web, access markets sell access to compromised endpoints. For only $10, an attacker can purchase access to a backdoor (“bot”) or to usernames, passwords, and cookies exfiltrated from a machine by stealer malware (“logs”). In theory, the attacker can gain access to any account to which the compromised endpoint is logged in. (A Cybersixgill research project last year found that major ransomware groups may be using these markets to establish initial access in their attacks.)
We chose the three leading producers of continuous glucose monitors (CGM) as case studies. These implanted sensors measure blood sugar levels, offering patients and medical professionals a more complete understanding of a patient’s blood sugar records than the snapshot provided by finger-pricking several times a day. The data that they collect is available on online patient portals.
Collectively, these markets listed access to 1,241 patient accounts for Abbott, Medtronic, and Dexcom CGMs from April 1, 2022 to April 1, 2023. Attackers that purchase access to these listings could theoretically gain access to patient glucose readings and other information stored in the account.
 Figure 1: Logs from an endpoint logged into Dexcom’s uam1[.]dexcom[.]com for sale on an underground access market.
Figure 1: Logs from an endpoint logged into Dexcom’s uam1[.]dexcom[.]com for sale on an underground access market.
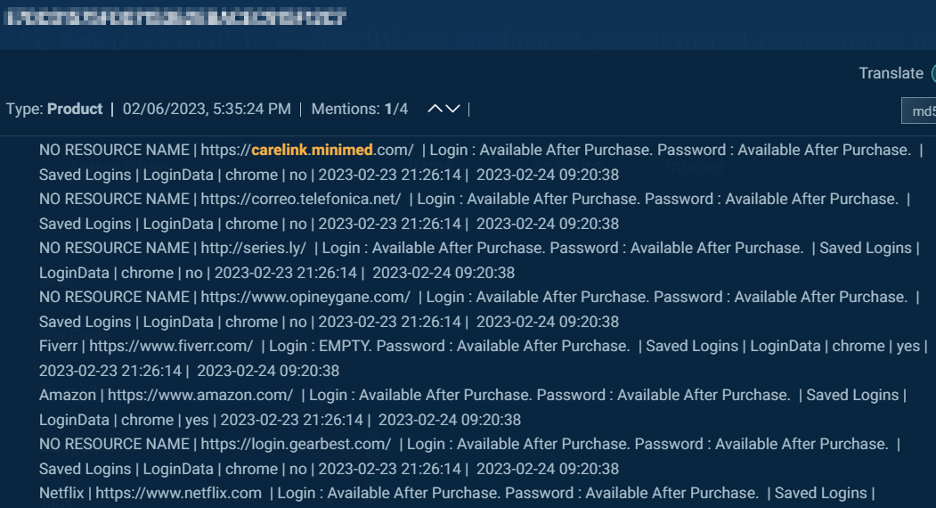 Figure 2: A bot from an endpoint logged in to Medtronic Carelink’s carelink[.]minimed[.]com for sale on an underground access market. Note that the bot also contains logins to accounts such as Amazon, Netflix, and Telefonica.
Figure 2: A bot from an endpoint logged in to Medtronic Carelink’s carelink[.]minimed[.]com for sale on an underground access market. Note that the bot also contains logins to accounts such as Amazon, Netflix, and Telefonica.
 Figure 3: Logs from an endpoint logged into Abbott Freestyle Libre’s freestylelibre[.]com for sale on an underground access market. Note that the bot also contains logins to an account for CaixaBank.
Figure 3: Logs from an endpoint logged into Abbott Freestyle Libre’s freestylelibre[.]com for sale on an underground access market. Note that the bot also contains logins to an account for CaixaBank.
We stress that this does not show that these accounts or their underlying software were “hacked,” nor does it reveal any vulnerabilities in the devices or account software. Rather, it highlights the complex attack surface of PHI: patient data was potentially compromised because it was accessible from an endpoint that was compromised.
The regulatory risk
Even though they have no ability to prevent or detect a malware attack on a patient computer, heathcare providers may still assume some of the risk in these scenarios. That is, HIPPA measures mandate that systems handling PHI provide measurable security safeguards as per the HIPAA “Security Rule”, for patient accounts. Security control measures such as multifactor authentication and monitoring for suspicious login and behavior, for example, might effectively mitigate much of the risks posed by access markets.
Patients must also act responsibly when it comes to handling personal accounts with sensitive data. This includes reviewing and following the vendor’s security policy and putting the guidelines into practice. Steps like unique and complex passwords and cautiousness with malicious attachments and downloads that could infect their systems with malware will help increase the protection of PHI.
Ultimately, convenience does not need to come at the expense of security. Through adequately mapping and assessing threats, healthcare providers can mitigate the risk of compromised protected health information.
)
)
)
)