)
Cars are lucrative yet fast-moving targets for hackers. As they transform from combustion engines into sophisticated computers-on-wheels, threat actors have a larger attack surface to exploit. However, the automotive industry has also invested considerably in securing cars, seeking to lock attackers out, both physically and virtually.
Threat actors share information and tools related to automobile hacking and theft on several dedicated underground forums. They also sell stolen cars, equipment for auto theft, fake driver's licenses, and bank certificates for car loans.
Improved tools and more sophisticated techniques may have contributed to the significant recent rise in US vehicle theft, which increased from ~888,000 in 2020 to over 1 million in 2022.
This article examines activity on underground automotive forums, including sales of various tools, stolen cars, and fraud services.
Tools
Master Keys: A master car key can open the doors and start the ignition on multiple vehicles. While these keys are reserved exclusively for auto industry professionals and locksmiths, thieves can readily obtain them to steal cars.
 Figure 1: A threat actor looking for a master car key
Figure 1: A threat actor looking for a master car key
 Figure 2: A threat actor selling BMW G-series keys
Figure 2: A threat actor selling BMW G-series keys
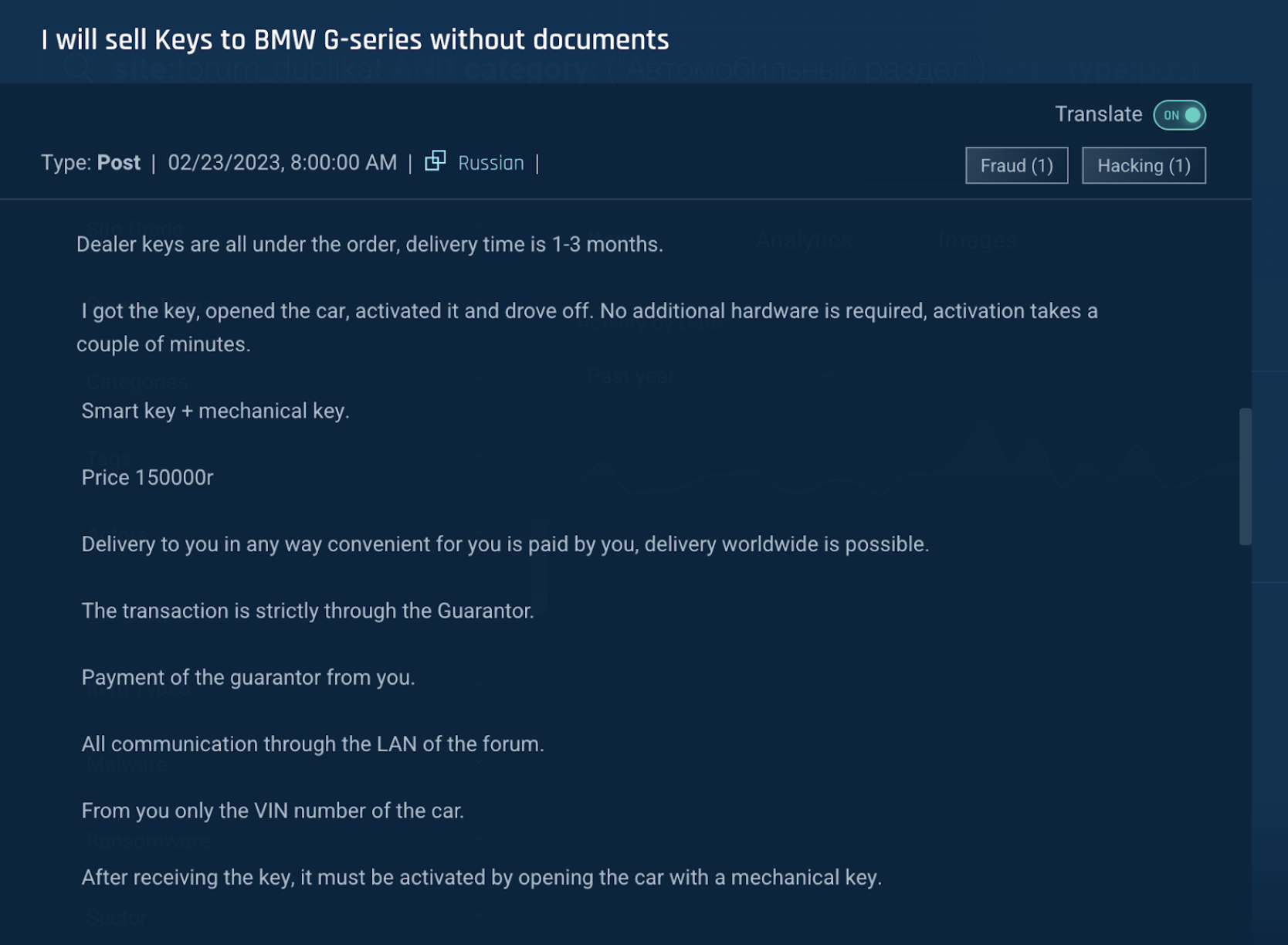 Figure 3: A threat actor selling BMW G-series master keys for 150,000 rubles (~$1,974)
Figure 3: A threat actor selling BMW G-series master keys for 150,000 rubles (~$1,974)
 Figure 4: An image of the keys for sale
Figure 4: An image of the keys for sale
 Figure 5: The actor explains how to activate the key for a specific automobile
Figure 5: The actor explains how to activate the key for a specific automobile
Code grabbers: Many new and late-model cars are equipped with keyless entry/start fobs, which enable motorists to start the vehicle without removing the devices from their pockets. Thieves use devices called code grabbers to intercept signals between key fobs and the car. They can then use code grabbers to repeat the signal to the car, spoofing the key fob and activating the automobile. Code grabbers are readily available online and on underground forums.
 Figure 6: A request for a Mercedes code grabber on an automotive hacking forum
Figure 6: A request for a Mercedes code grabber on an automotive hacking forum
 Figure 7: A threat actor sells code grabbers for brands such as Lexus, Toyota, and BMW.
Figure 7: A threat actor sells code grabbers for brands such as Lexus, Toyota, and BMW.
Services
Threat actors advertise various automobile fraud services, enabling others to carry out more sophisticated thefts.
Registration fraud: Threat actors carry out fraudulent sales and re-register a car in the name of a new owner through the Department of Motor Vehicles (DMV). One actor offering this service explains (figure 8) that once a car’s registration changes, the new “owner” can sell the car, tow it, or report it as stolen to convert it into cash.
 Figure 8: Registration fraud services
Figure 8: Registration fraud services
Fake documents: Fraudsters also sell fake documents that enable actors to purchase and operate vehicles. These include fake driver's licenses, bank loan documents, and car insurance forms.
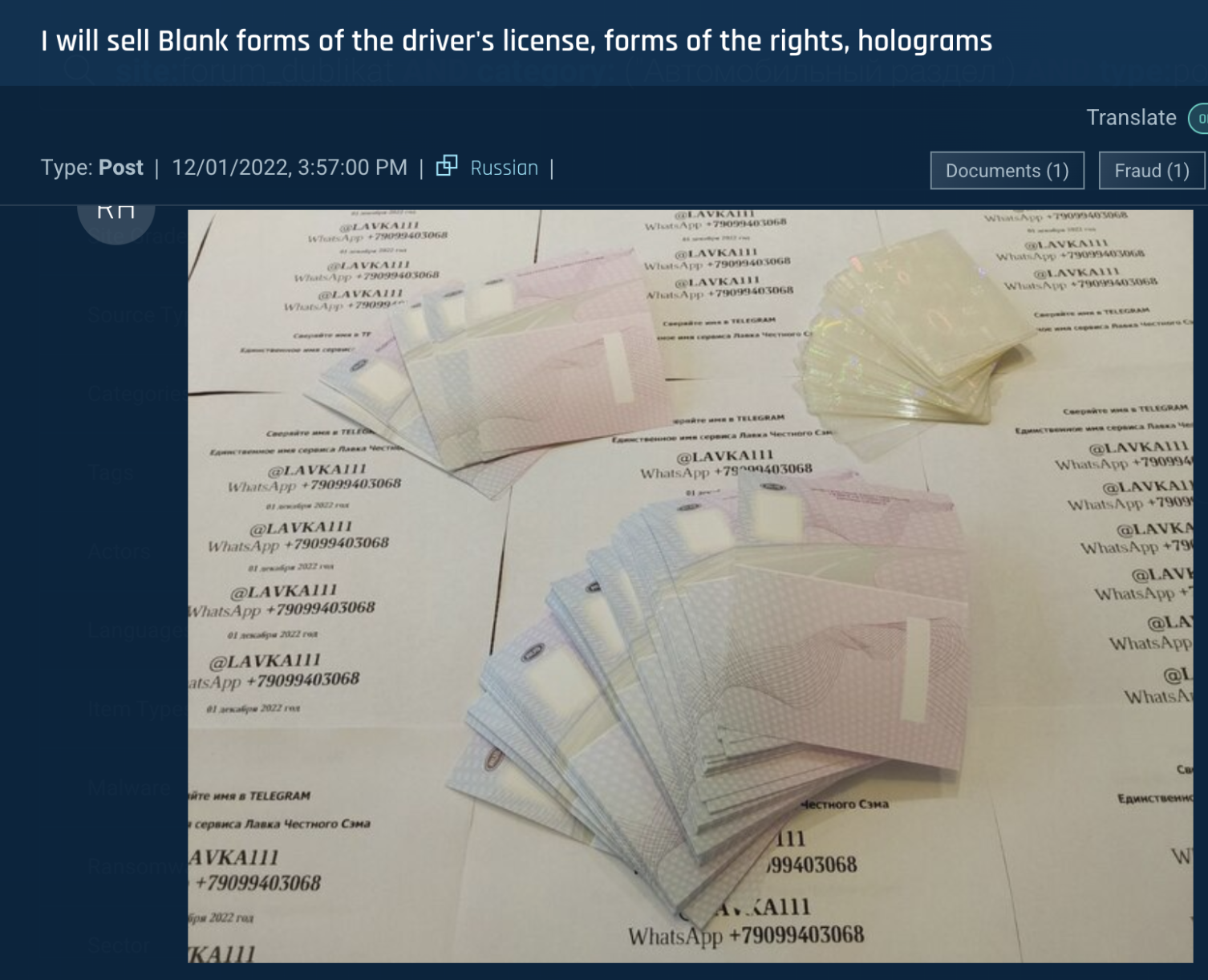 Figure 9: Fake driver's licenses and vehicle registration documents offered for sale on the underground
Figure 9: Fake driver's licenses and vehicle registration documents offered for sale on the underground
Stolen Cars: Several actors even sell vehicles on underground hacking forums. While they do not generally mention if they have legal possession of these cars for sale, several indicators signal that they are illicit (beyond the obvious fact that anything sold on the dark web is inherently suspicious). First, in the example below (figure 10), the price is suspiciously lower than the vehicle’s recommended value on the second-hand market.
Second, sellers of stolen vehicles generally only list the price and mileage. They omit essential information, such as the number of previous owners, insurance details, and registration/test data.Finally, these transactions are cash-only, preventing a paper trail that law enforcement can follow.
 Figure 10: A presumably stolen vehicle offered for sale on an underground automotive hacking forum
Figure 10: A presumably stolen vehicle offered for sale on an underground automotive hacking forum
Furthermore, prospective buyers look for cars without documents or “unnecessary questions” (figure 11).
 Figure 11: An actor in England looks to purchase a car illegally
Figure 11: An actor in England looks to purchase a car illegally
Conclusion
Over the last decade, automobiles have transformed into complex computer platforms. While this provides considerable convenience to drivers, it has also expanded the threat landscape for threat actors to exploit.
Our analysis of underground automotive hacking forums has shown that car hackers use a combination of innovative technologies--such as signals interception and time-worn methods, such as social engineering and forgery, in order to obtain and operate vehicles illegally. Car manufacturers must ensure that new features do not open the door for attackers by implementing security and tracking chatter among hackers.
Cybersixgill automatically aggregates data leaks and alerts customers in real time.
)
)
)
)